In this article, we’ll look at how to configure UniFi Firewall Rules so that you can build a secure, home or small business network. There are various options we’ll look at, from the source and the destination, to the type (LAN In, LAN Out, LAN Local, etc).
This is arguably the most important setup of any network, as firewall rules determine exactly what each device on your network can access, so this guide will help explain the key options you’ll use to configure your network.
Automatic Firewall Rules for UniFi Networks
Ubiquiti has made it extremely easy to auomatically create firewall rules for some of your devices. When you create a VLAN, there are three advanced options: Guest Network, Isolate Network, and Allow Internet Access.
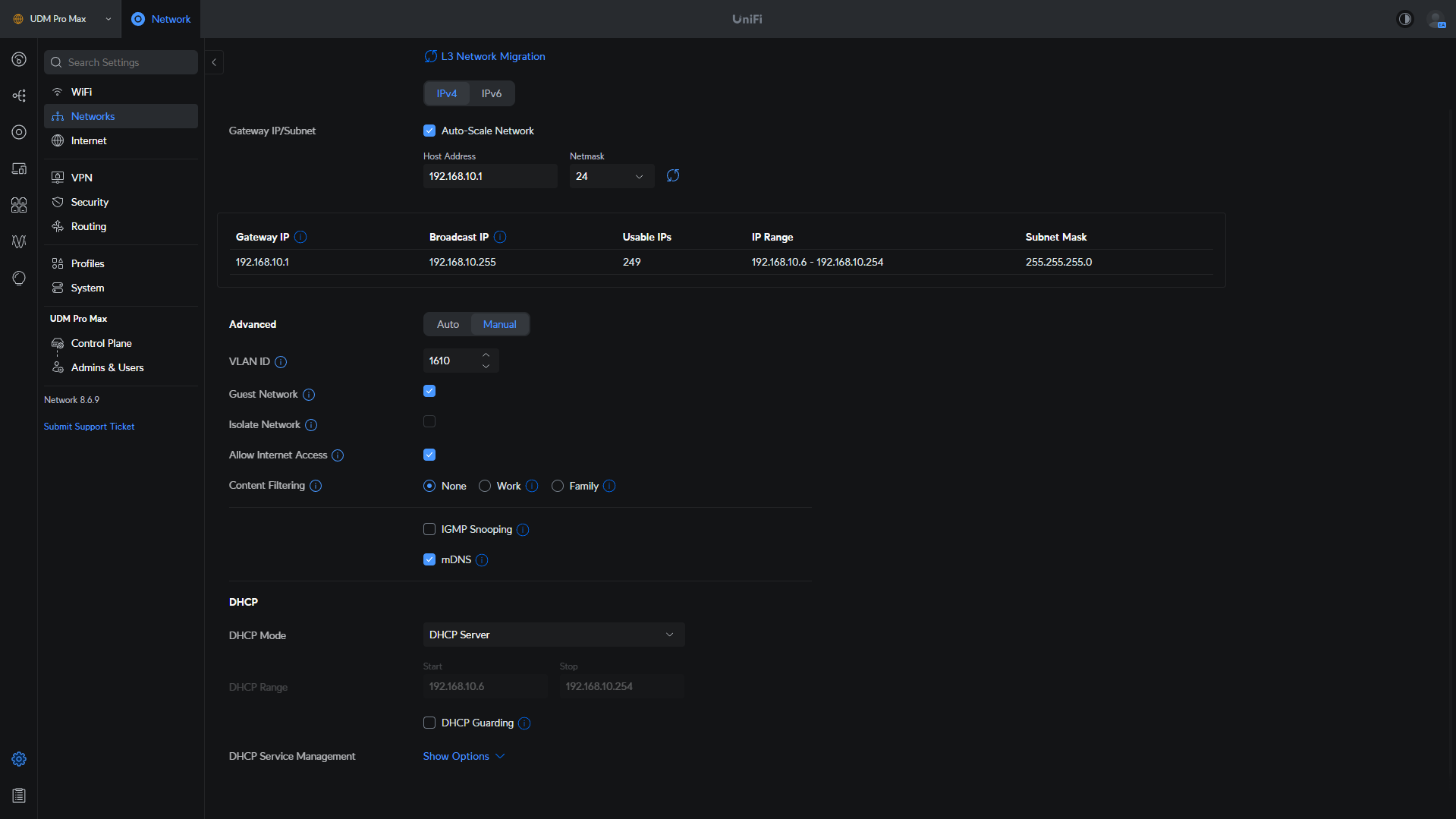
Each option will automatically create firewall rules for this specific network, which is an easy way to ensure that a base level of access is granted and everything else is revoked.
Guest Network: Firewall rules are created for the guest network that allows things like the hotspot portal and DNS, while automatically blocking traffic for your local networks and more.
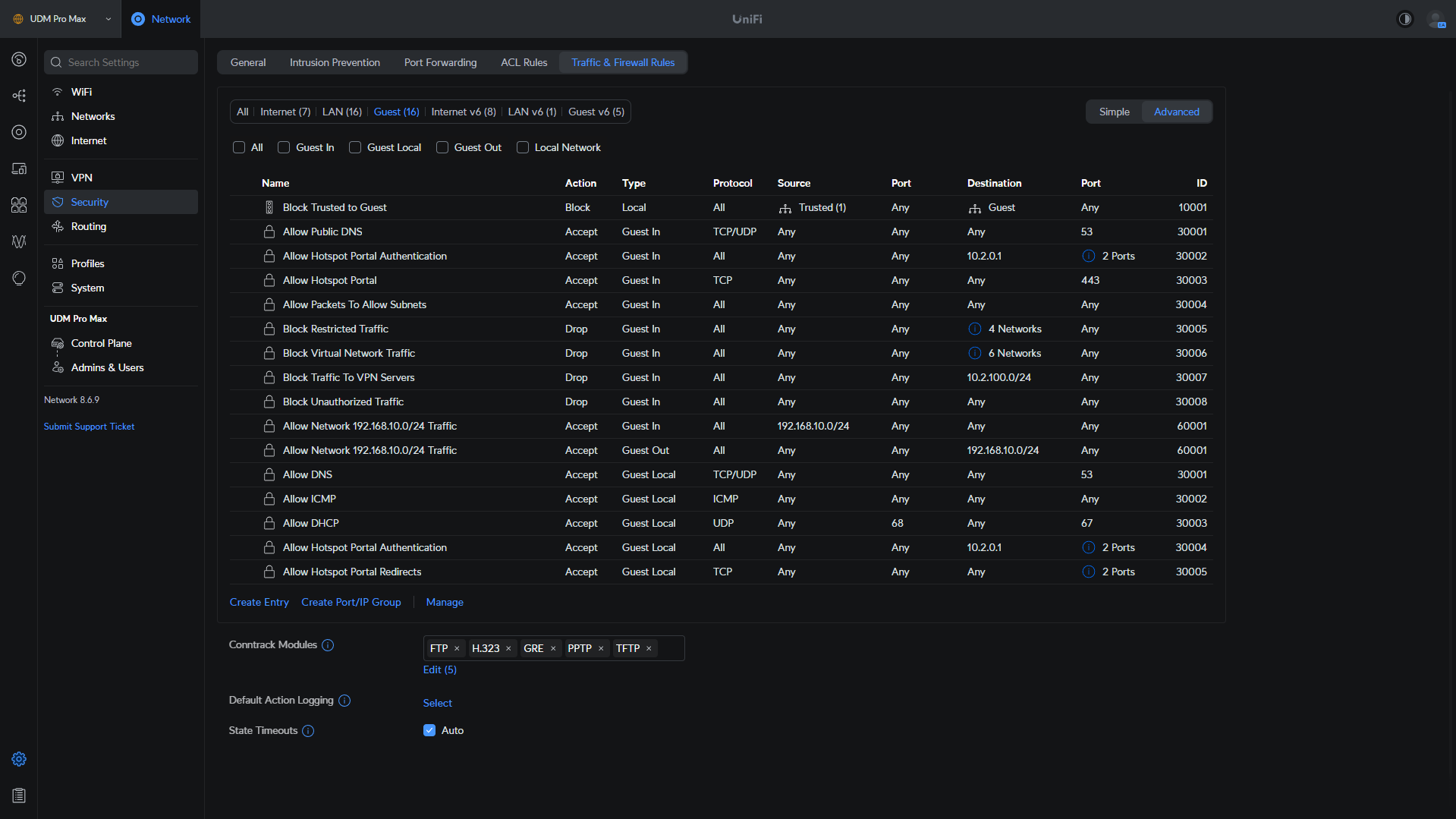
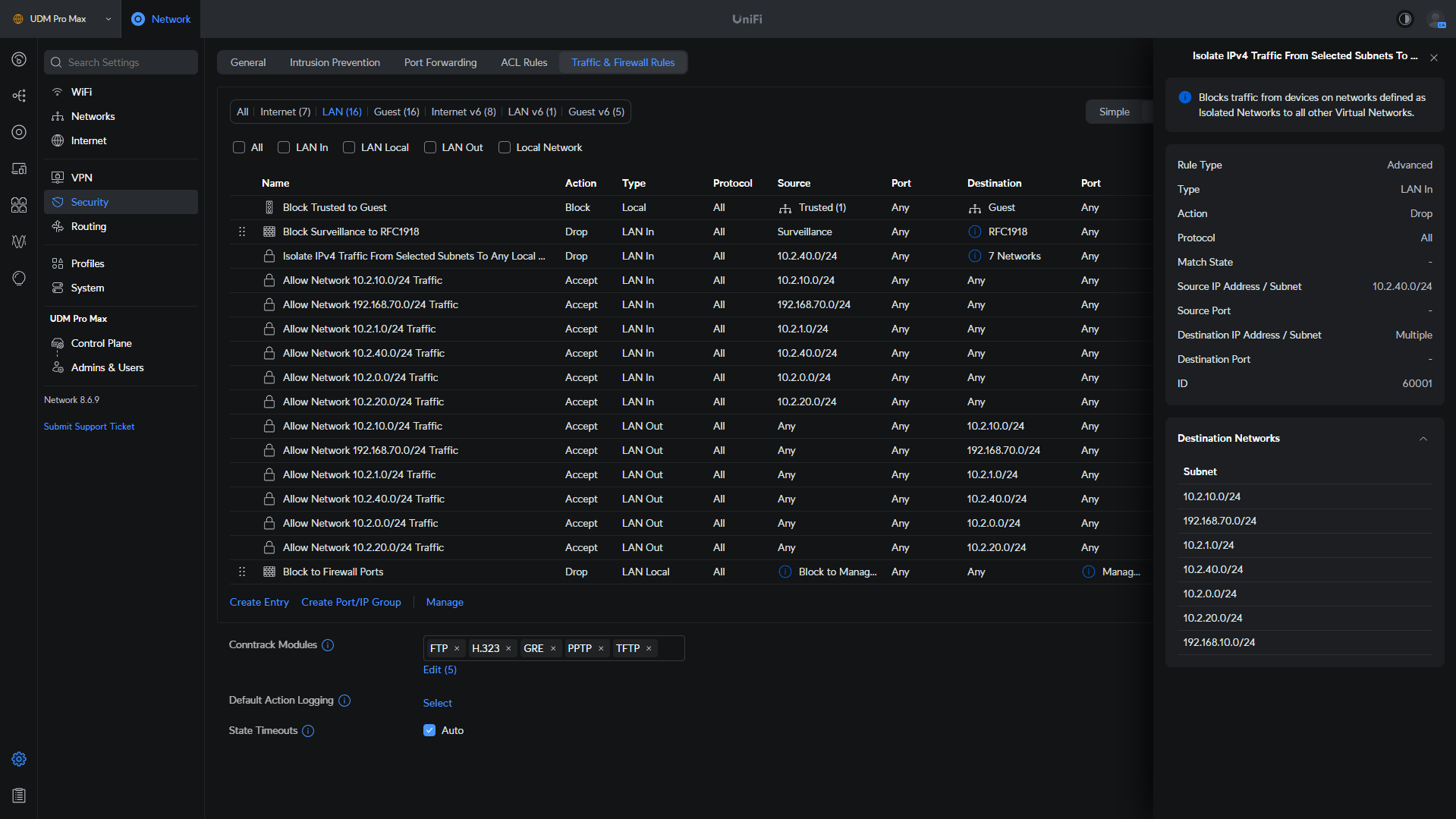
Isolate Network: A rule is automatically created that will isolate traffic for this specific VLAN going to any other VLANs that are configured. Please keep in mind that this isolates traffic ONLY to other VLANs.
Allow Internet Access: By unchecking this option, the VLAN will not be allowed to access the external internet, but local traffic will still function as expected.
How to Configure UniFi Firewall Rules for a Secure Network
There are two main options you can use to configure UniFi firewall rules – simple and advanced. You’ll use both of these to create different types of rules, and generally, a setup will have multiple simple/advanced rules.
Firewall rules execute from top to bottom, so as you create rules, you’ll have to add allow rules above deny rules or the traffic will be blocked. This is generally used for cases where you want to punch holes (example: block all traffic from the IoT VLAN to the LAN VLAN, but allow one specific IoT device to access the LAN network).
How to Configure Simple Firewall Rules
Simple firewall rules are designed to be…simple. Generally, you can create a basic firewall rule to block or allow traffic from various sources (IP address, local network, etc) to another type (IP Address, local network, internet, etc).
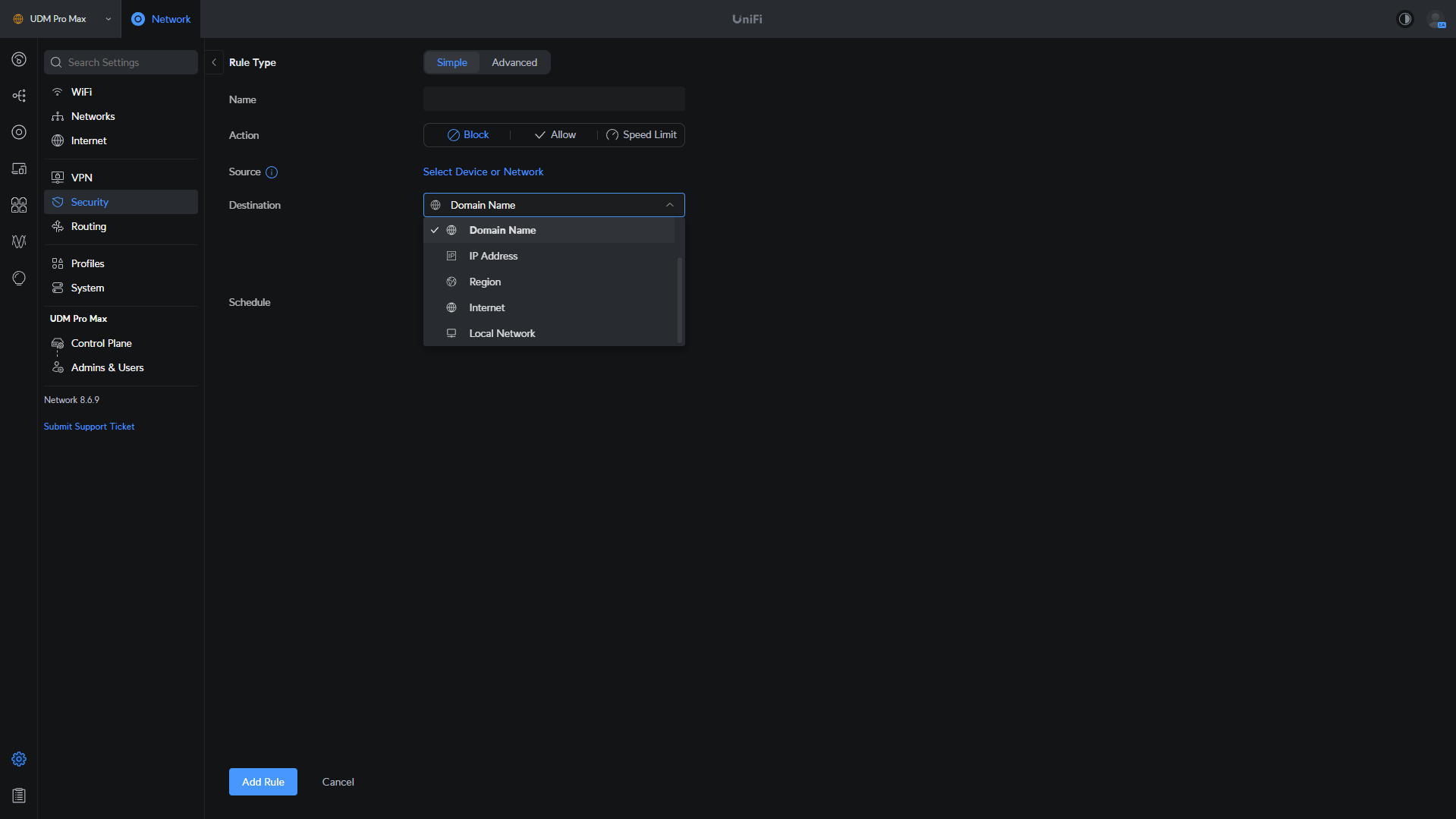
If you simply want to block traffic from one VLAN to another or multiple VLANs, a basic firewall rule will work well. You’ll have to select a source (where traffic is coming from), and a destination (where traffic is going), then determine the direction of the block (source to destination, destination to source, or both directions).
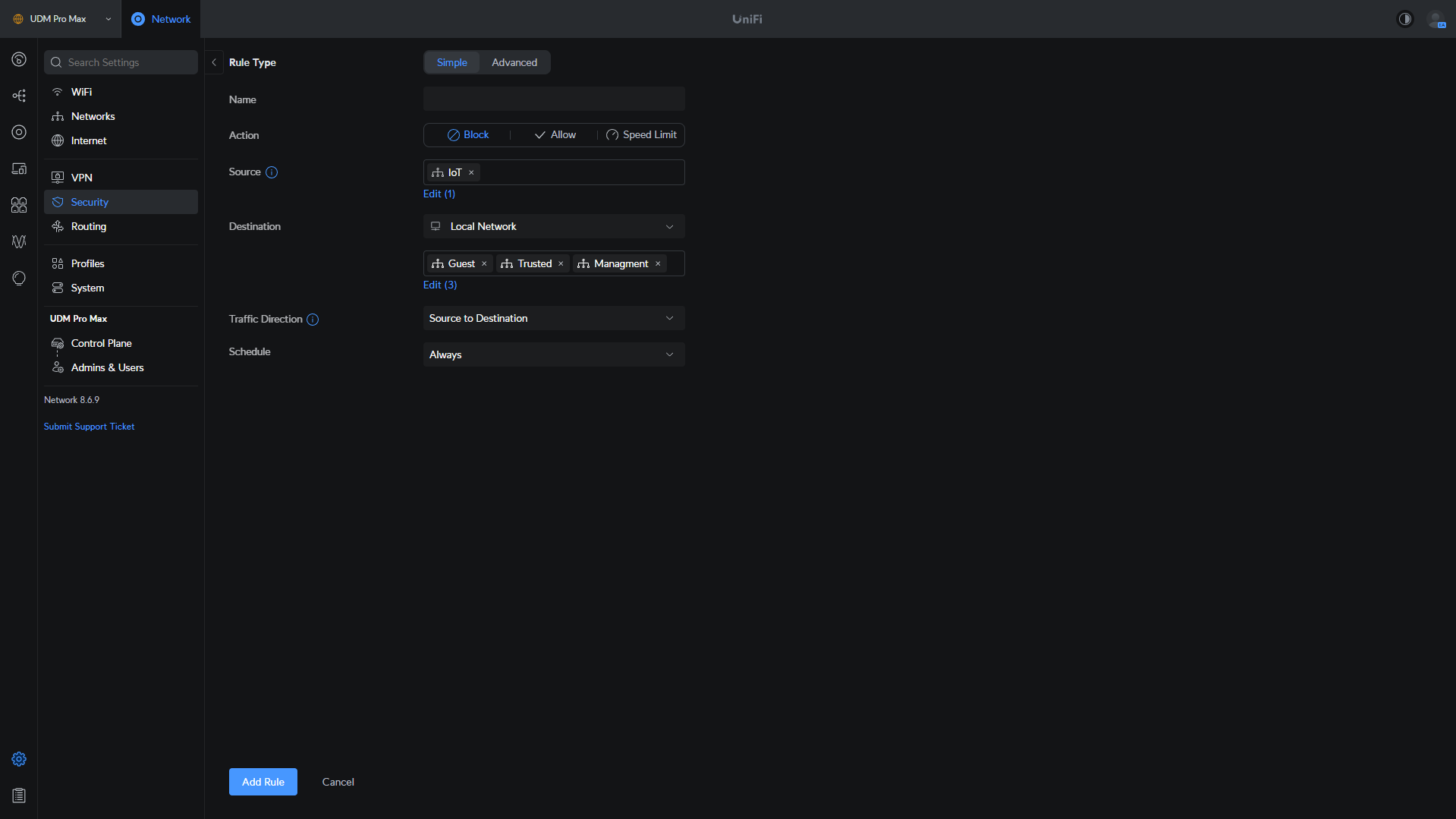
The downside of simple rules is that if you want to really modify anything, you’ll have to use an advanced rule. In general, I’d suggest starting with advanced rules so that you can modify your UniFi firewall rules to function properly, and be easily customized in the future.
How to Configure Advanced Firewall Rules
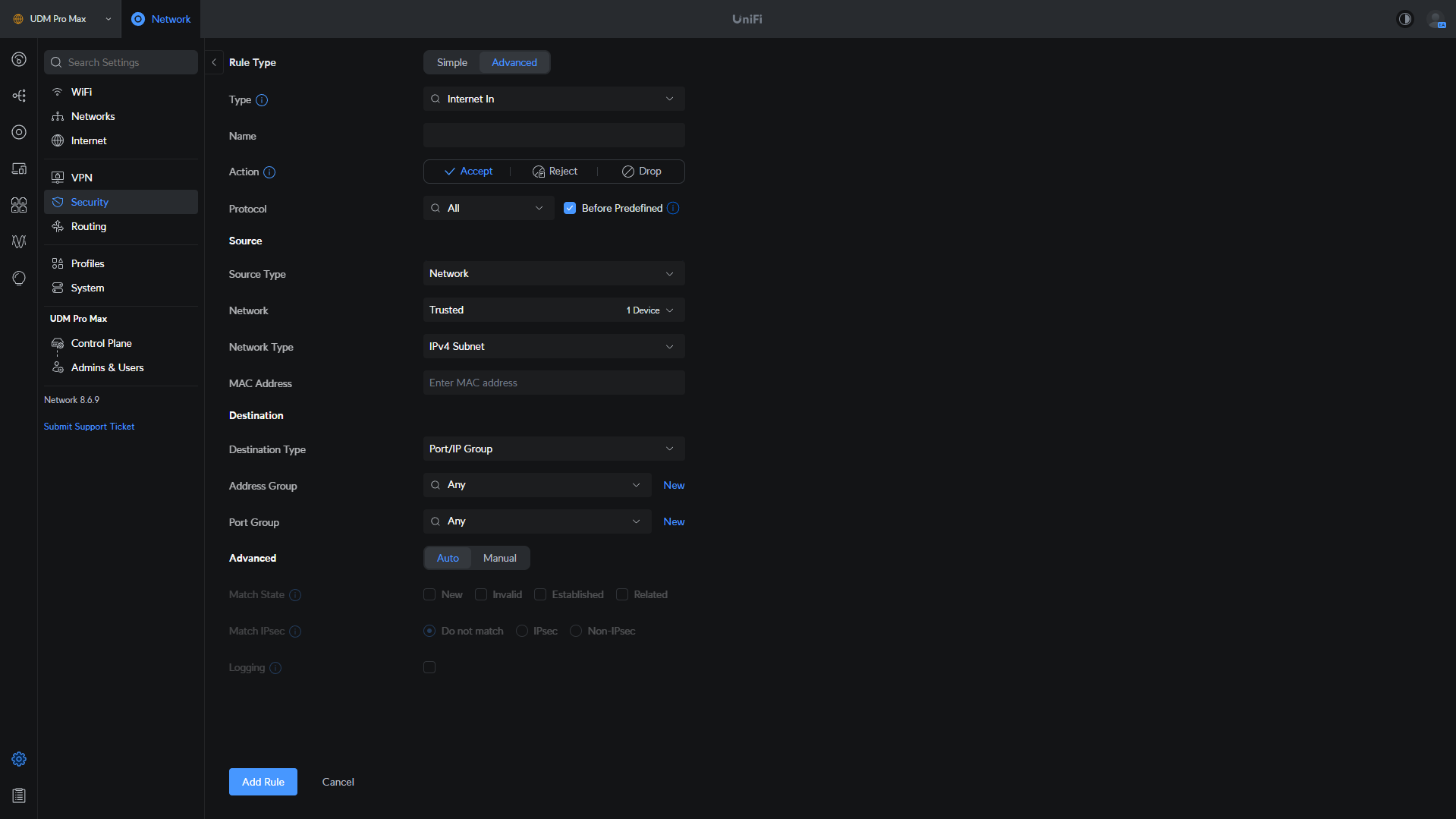
Advanced firewall rules, while being more complicated, are significantly more powerful and allow for much greater customization. With that said, there are a few important points that have to be made before configuring any rules.
- Source: This is where the traffic will be coming from.
- Destination: This is where the traffic will be going.
For the source and destination, it can consist of an IP address, network (one only), or port/IP group.
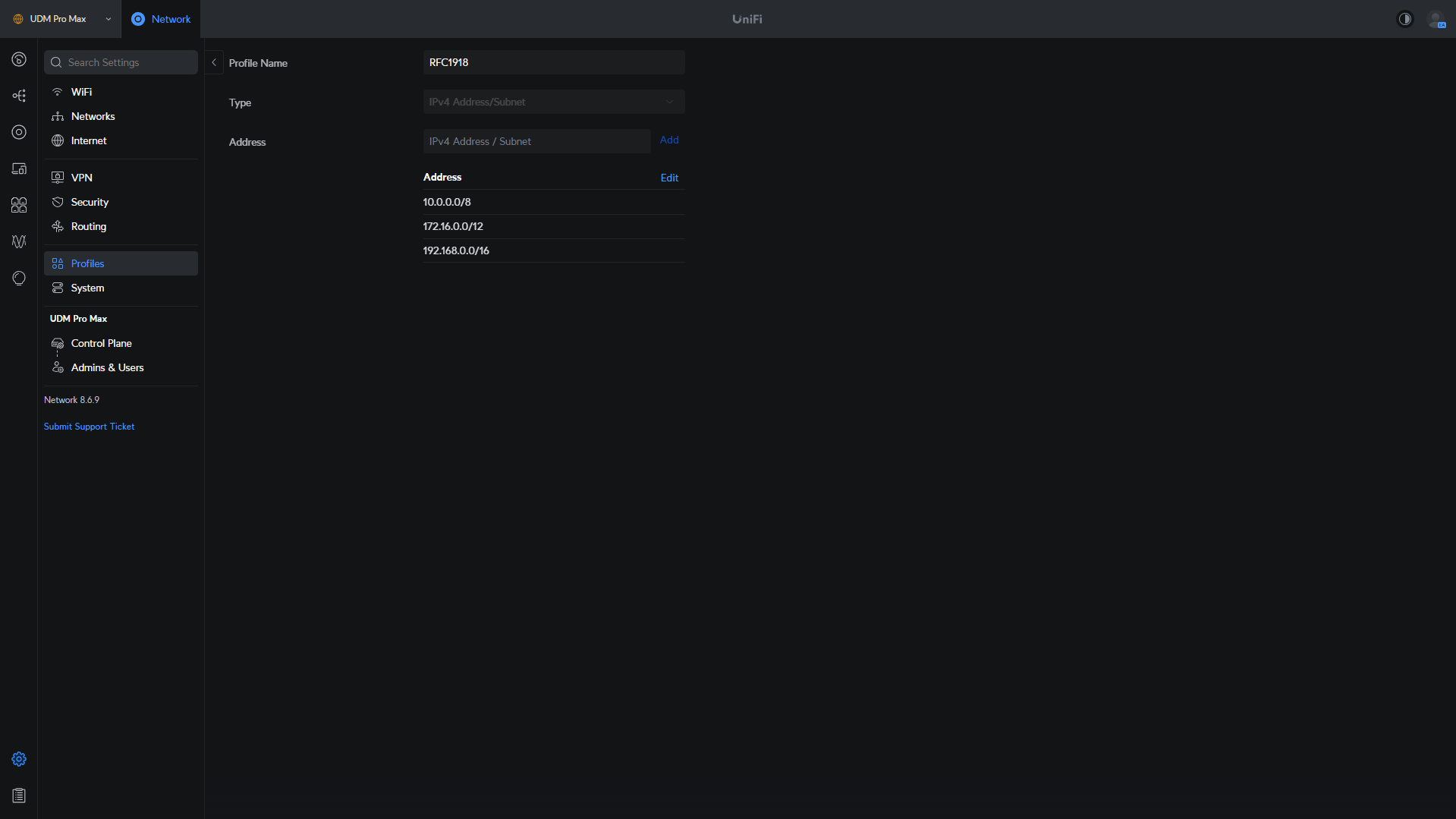
If you want to use multiple subnets, your best bet is to use an IP group so that you can define multiple IP addresses or subnets, and block or allow traffic for all of them. A common option for firewall rules is to create an IP group for RFC1918, consisting of 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16. This will be a group for all local IPv4 addresses that can be used.
You can also use Port Groups if you’d like to block or allow traffic to specific ports. A common firewall rule created is to block traffic to the management interface for the UniFi router, so you’d create a Port Profile for TCP ports 22, 80 and 443, and use it with a LAN Local rule.
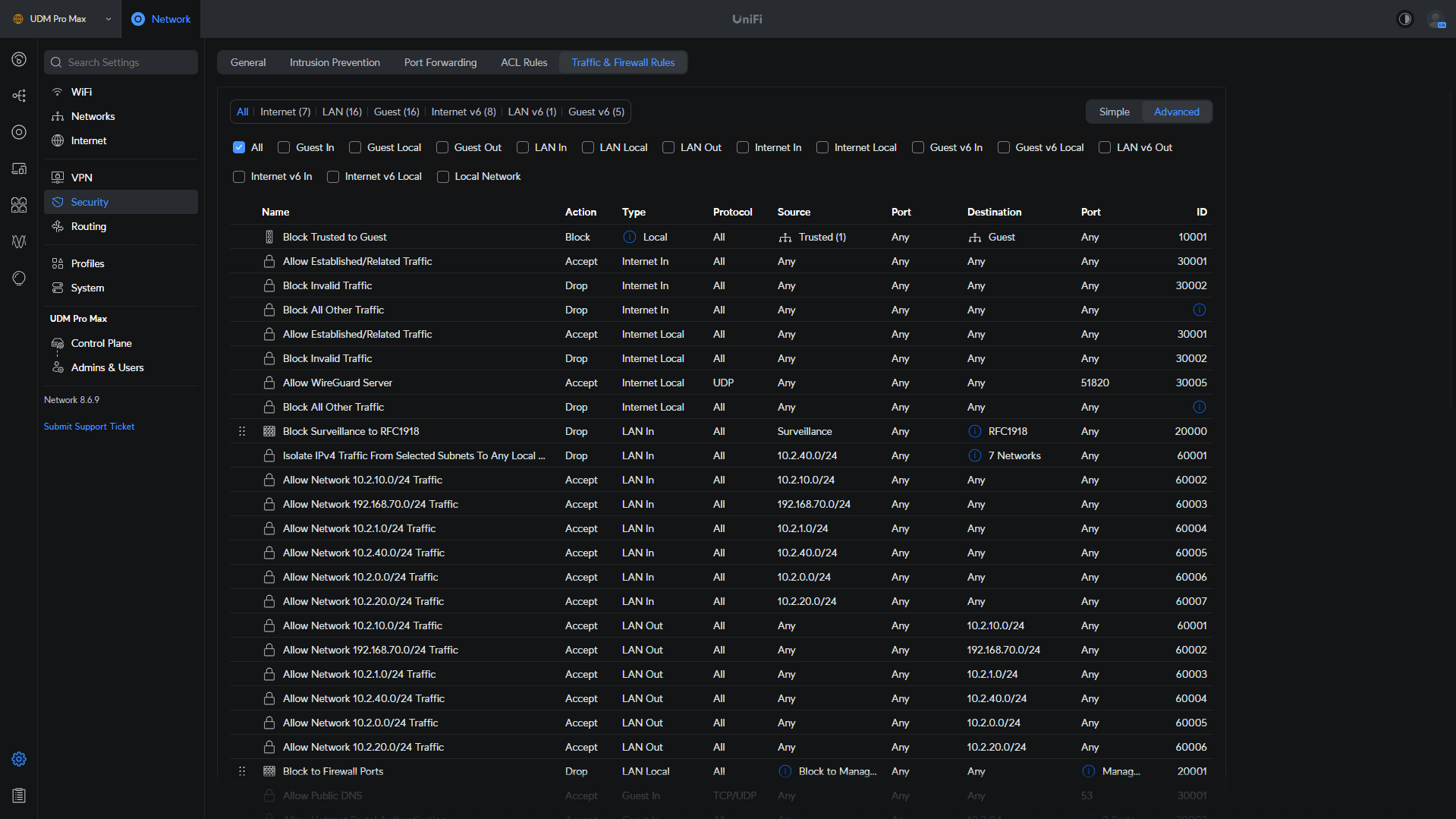
Firewall Rule Types (LAN In / LAN Out / LAN Local)
The biggest confusion around UniFi Firewall Rules generally comes from the type, as you can select LAN In, LAN Out, LAN Local, Internet In, Internet Out, and Internet Local (with the same options for IPv6). These rules are extremely important as they determine exactly which, and what type of traffic gets allowed or blocked.
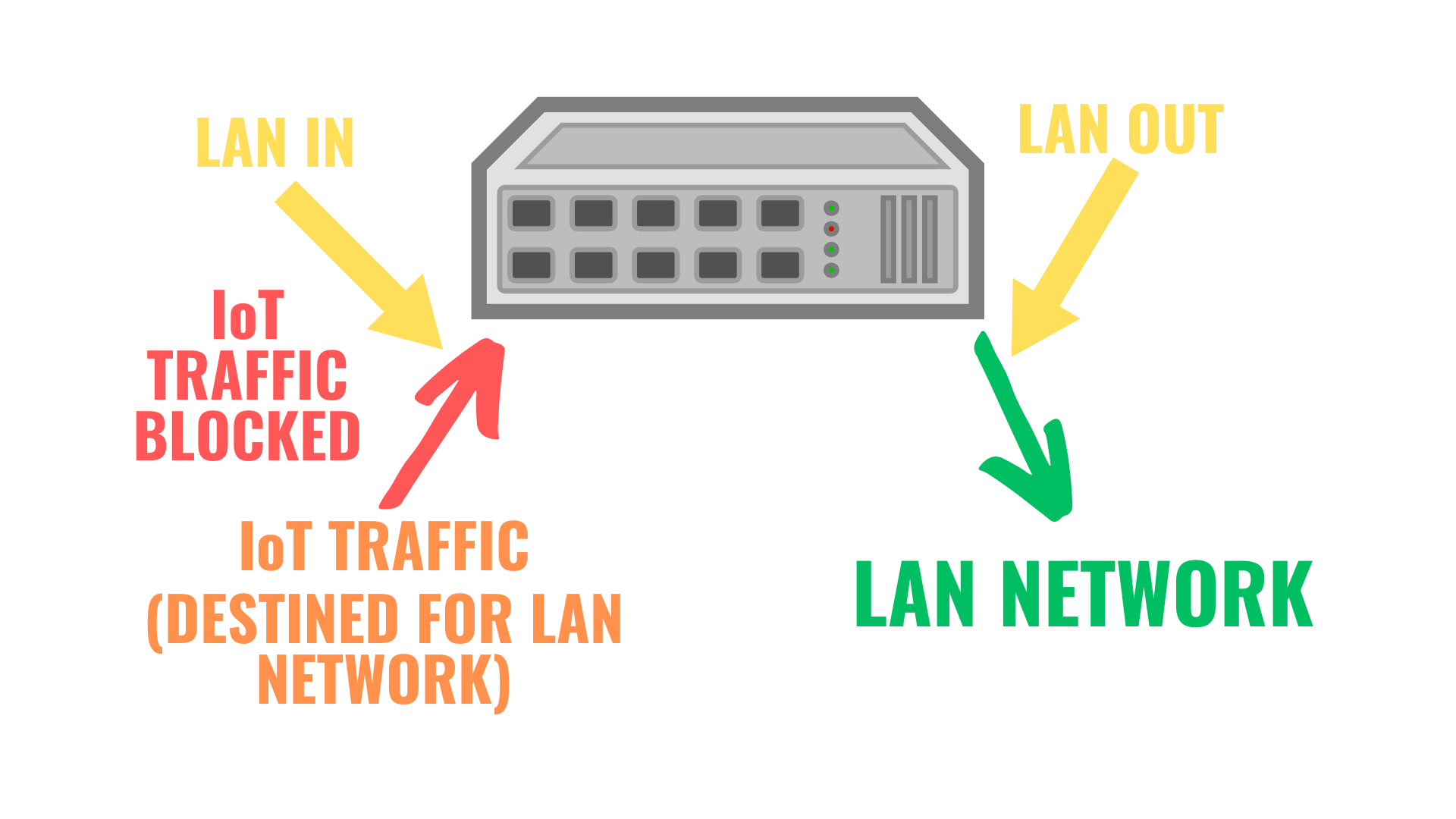
- LAN In: Traffic is blocked going from the source IN to the firewall.
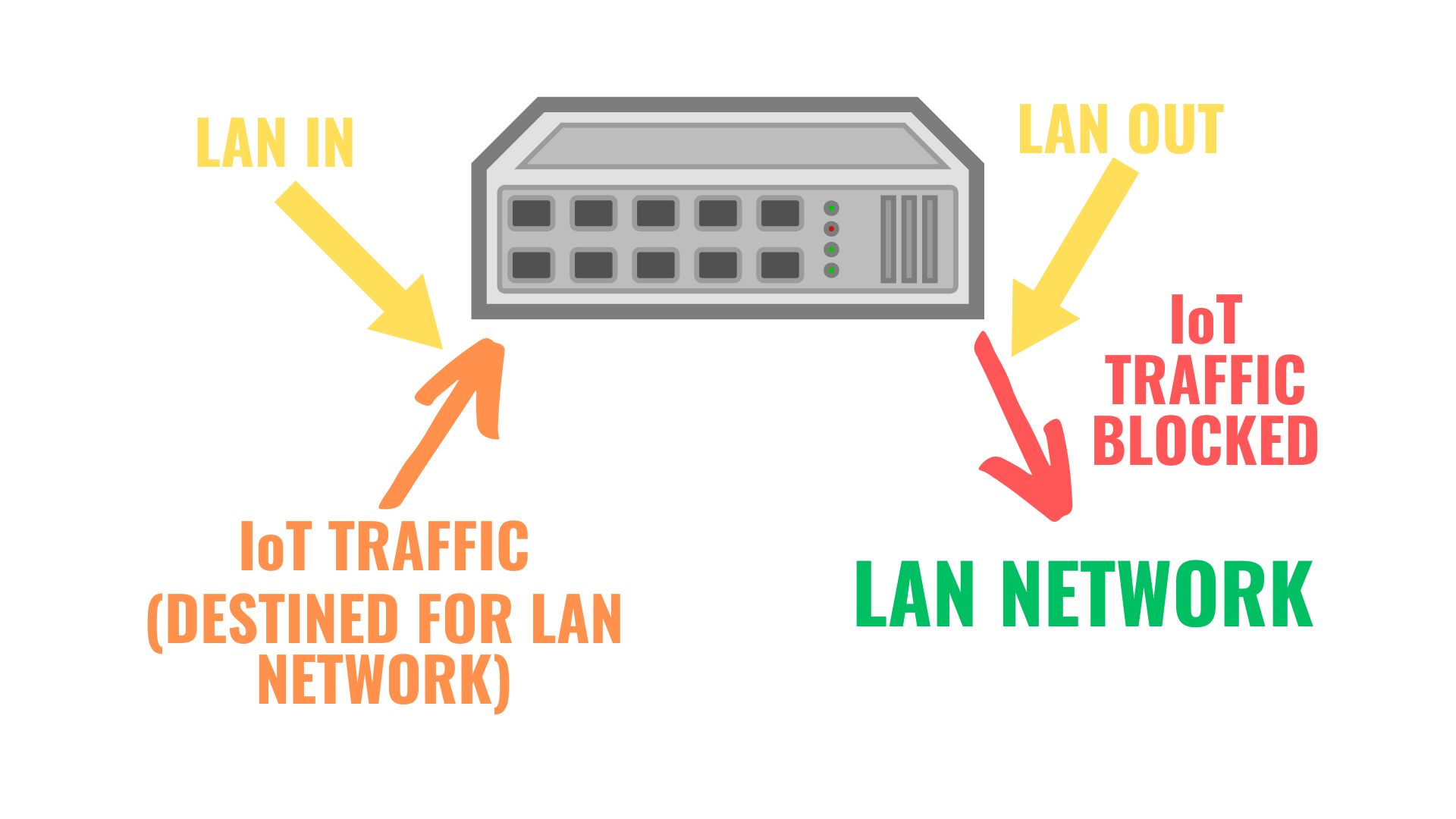
- LAN Out: Traffic goes IN to the firewall, then is blocked when it is going OUT of the firewall.
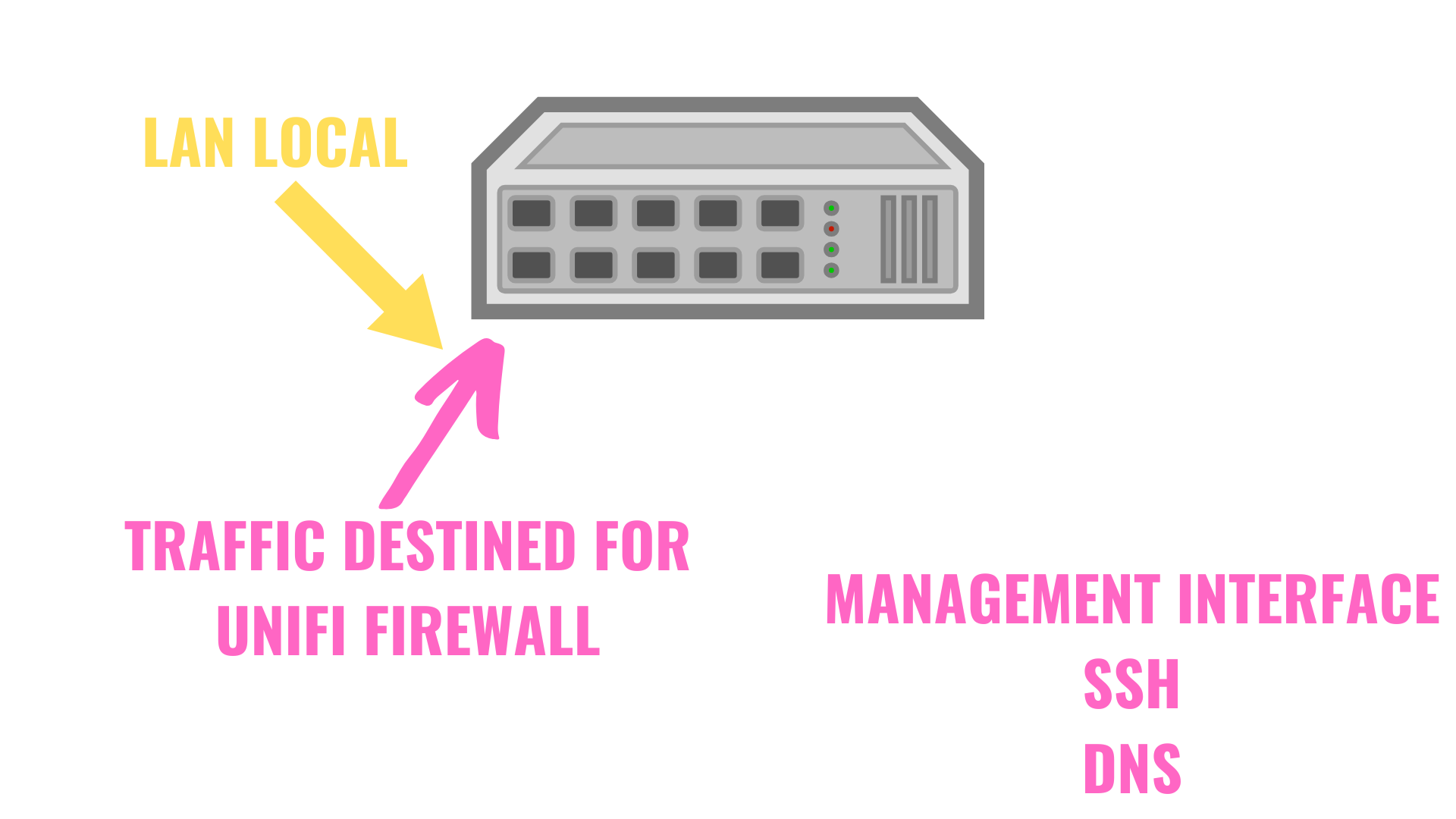
- LAN Local: Traffic is blocked only if it is DESTINED for the firewall itself (management interface, SSH, DNS, etc).
Generally, for LAN to LAN communication, you’ll use LAN In rules, as you want traffic being blocked on it’s way IN to the firewall. For example, if you want to block traffic from the IoT Network to the LAN Network, you’ll use LAN In.
If you were to use LAN Out, traffic will still be blocked, however, it will be blocked after it has already gone through the firewall. To avoid unnecessary routing, you should use a LAN In rule to avoid this problem.
LAN Local is slightly different as it is traffic that is destined for the firewall itself. This will mainly be used for things like blocking the management interface, SSH access to the firewall, DNS (if it’s running on the router), and just about anything else running on the firewall itself.
The exact same principals apply to internet traffic, but it’s generally coming from the opposite direction. For example, if you’re port forwarding a specific port and want to limit that traffic down to a set of IP addresses, you’ll use an Internet In rule, as that will apply to the traffic coming from the internet into the firewall.
Internet Out is the opposite of that – traffic coming from the UniFi Firewall, going to the internet. Internet Local is for traffic originating from the internet going into the firewall itself (an example being exposing the management interface to the internet or a VPN server).
Creating Firewall Rules for VPN Traffic
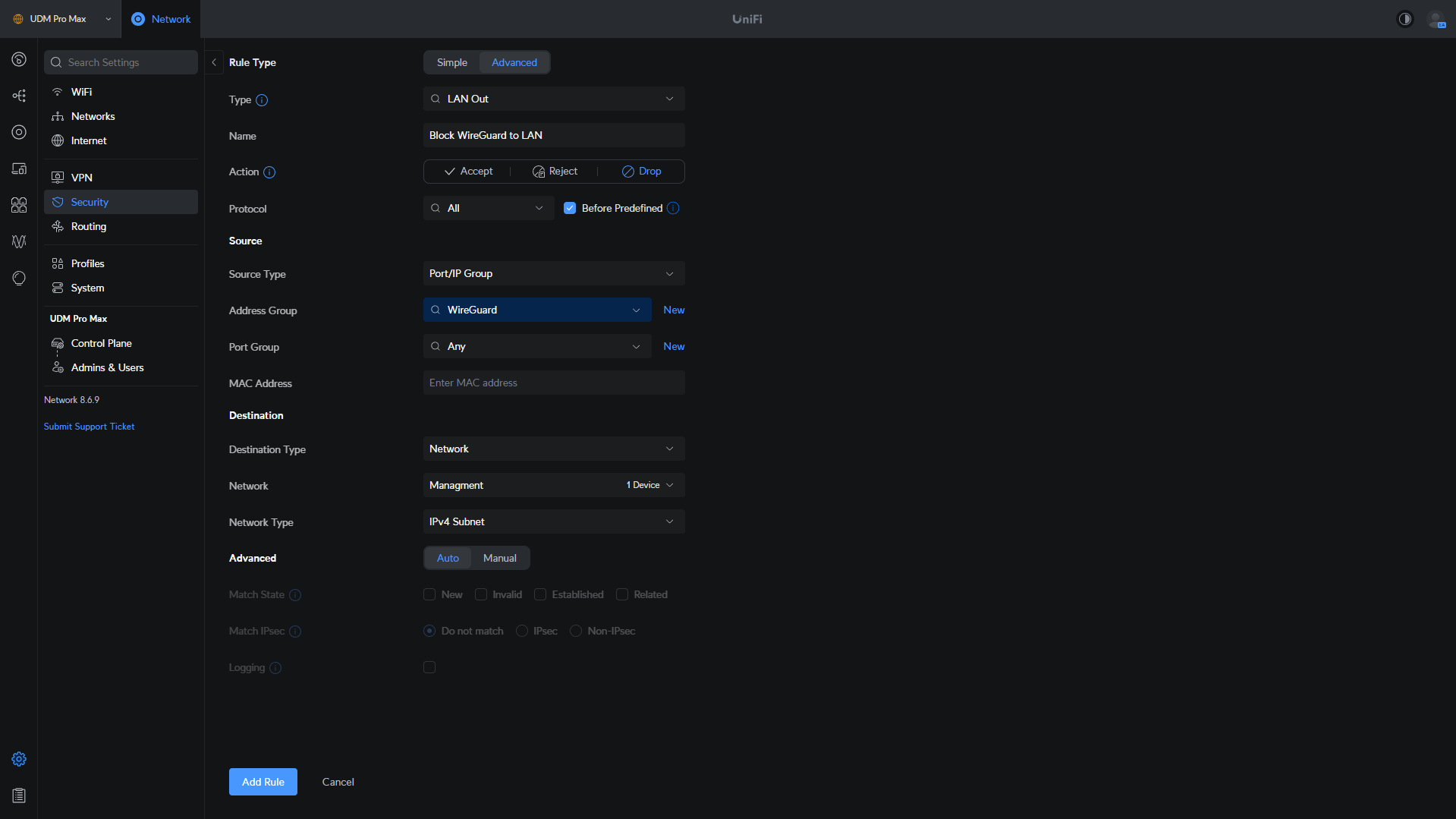
The biggest confusion after learning about the types of UniFi firewall rules used for LAN/Internet traffic is for VPN traffic. When you’re hosting a WireGuard or OpenVPN server on your UniFi device, the type of rule must be LAN Out if you’d like to limit traffic from a VPN device to a local network.
This is because the VPN server is hosted on the UniFi router, so rather than traffic going into the firewall, traffic is originating from the router itself. Therefore, if you want to block traffic from a VPN device, you’ll use LAN Out, or Internet Out.
Final Thoughts on Firewall Rules for UniFi Devices
The actual UniFi firewall rules that you’ll use will start to make sense as you get the hang of how Ubiquiti handles them. Each firewall functions slightly different and the rules across devices are generally different, but this all starts to make sense as soon as you understand the differences between the type of rules you’d like to create. Thanks for checking out the article – if you have any questions, please leave them in the comments!




