In this tutorial, we will look at how to connect a Raspberry Pi to a WireGuard VPN Server.
I use Raspberry Pi devices for various different things with some of them being used off-site. Something that runs constantly is the Raspberry Pi I use to backup my Synology NAS off-site. I’ve always used OpenVPN for this, but after setting up and configuring WireGuard, I was interested in using WireGuard as my VPN protocol for my off-site backup.
The thing with WireGuard is it’s almost nothing like OpenVPN. The concept of client devices and server devices isn’t valid which makes accomplishing this task somewhat different than most people are used to. The good news is that it’s very simple to set up and configure. The majority of it is done by running a few commands and adding your config file, but there’s very little information online that will show you exactly how to do this. After you configure the WireGuard server on a Raspberry Pi stored on your local network, the instructions below can be used to configure a Raspberry Pi to automatically connect to that VPN server every time it’s turned on!
Instructions – Connect Raspberry Pi to WireGuard VPN Server
1. Run the commands below, in this specific order. To sum up, we are adding the WireGuard Debian installation source and then ensuring that it’s not used for regular Raspberry Pi OS packages. We’re then installing WireGuard.
echo "deb http://deb.debian.org/debian/ unstable main" | sudo tee --append /etc/apt/sources.list
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 04EE7237B7D453EC
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 648ACFD622F3D138
sudo sh -c 'printf "Package: *nPin: release a=unstablenPin-Priority: 90n" > /etc/apt/preferences.d/limit-unstable'
sudo apt-get update
sudo apt install wireguard
2. After we’re done installing WireGuard, we need to install the WireGuard tools. This, along with WireGuard, is how we will connect back to our WireGuard VPN Server.
sudo su
apt install raspberrypi-kernel-headers libelf-dev libmnl-dev build-essential git
git clone https://git.zx2c4.com/wireguard-tools
make -C wireguard-tools/src -j$(nproc)
make -C wireguard-tools/src install
3. Since we’re only connecting back to our VPN Server, we need to create a file where we will store our VPN profile information. To be clear, this is generated on the VPN server side. We are only copying the contents of the file so that we can authenticate with our VPN server. Create the file, add the contents, and then save the file.
nano /etc/wireguard/wg0.conf
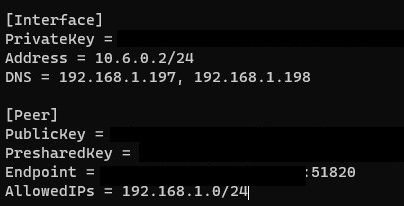
At this time, you have two different options. If you only want to connect to the VPN server, you can run the command below to connect. NOTE: The line below it in purple is what you will use to disconnect from the VPN.
wg-quick up wg0
wg-quick down wg0
If you want to connect to the VPN every time the Raspberry Pi is turned on rather than using the commands above, simply run this command and restart.
sudo systemctl enable wg-quick@wg0
There are a few additional items that you want to ensure that you have configured before restarting.
- Since this Raspberry Pi will most likely be remote, it’s a good idea to configure a persistent connection so that it doesn’t disconnect from the VPN.
- This configuration will allow you to connect FROM your external network TO your local network. Your local network will be unable to connect to your external network if you don’t configure a static route. This is a very important step that a lot of people miss!
Conclusion
This tutorial is very basic but it’s super powerful. There are so many different things you can do with Raspberry Pi devices. Having the ability to automatically connect to your home network safely and securely will give you so many options.
Thanks for reading. If you have any questions, please leave them in the comments!