In this tutorial, we will look at how to set up WireGuard on Unraid. WireGuard is a fast and lightweight VPN protocol that is incredibly easy to set up on Unraid. After setting up the WireGuard-Easy application (which runs in Docker), you can complete the port forwarding, configure a new client, then modify the client settings and everything should work as expected.
In comparison to running WireGuard on pfSense or OPNsense, it’s significantly easier. However, I will admit that I prefer running WireGuard on my router (but that’s not an option for everyone).
How to Set Up WireGuard on Unraid
The process below will explain how to set up WireGuad on Unraid
1. Select Apps, then search for WireGuard and install Wireguard-Easy.

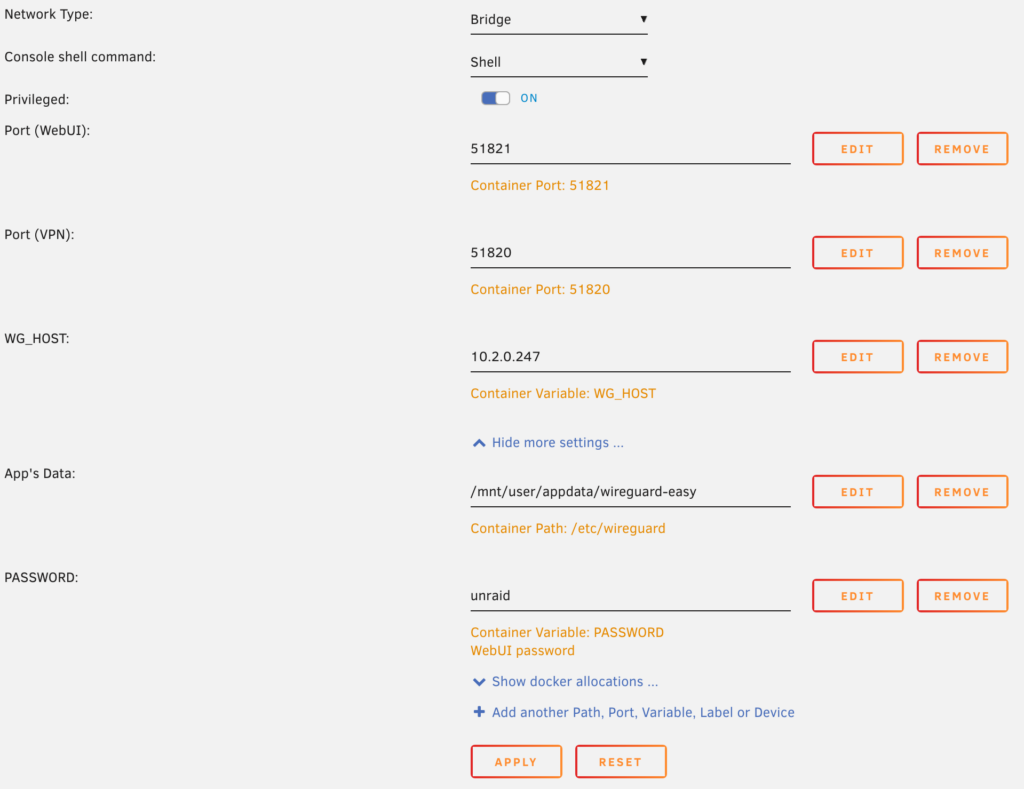
2. Almost all of the settings can stay as default, however, there are a few that we will modify.
- Set the WG_HOST variable to be the IP address of your Unraid server.
- If you’d like to modify the WireGuard port (51820), you can do that here.
- Change the default Web GUI password.
When you’re ready to install, select apply.
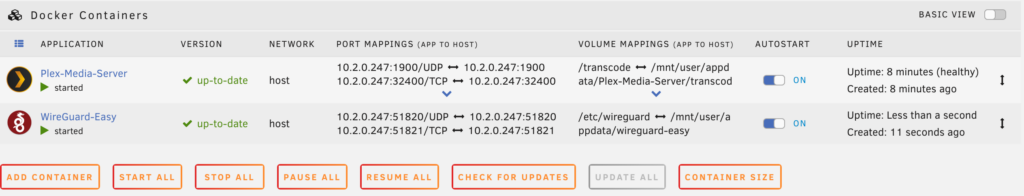
3. The container will now download and install! When it’s done installing, select Docker, then turn autostart on and ensure the container is started.
Port Forwarding Configuration
Since the WireGuard container will be hosted on the Unraid server, we must port forward UDP port 51820 to the Unraid server (if you’re using the default value). Port forwarding will be completely different on every brand’s router settings page.
This is a great guide that shows how to port forward on a few different brands of routers, but the best thing to do is try and google the name of your router and port forwarding. Example: Netgear port forwarding
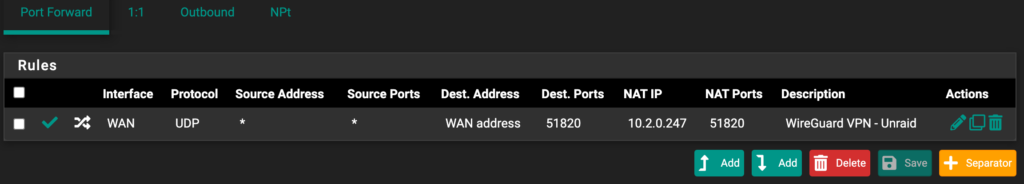
- Create a port forwarding rule for UDP port 51820 to your Unraid servers IP address. In the example below, 10.2.0.247 is the IP address of my Unraid Server.
NOTE: If you changed the port number to something different than 51820, make sure you use that port number.
Client Configuration
Now that the container is created and the port forwarding is complete, we can create a client. Creating a client using the WireGuard-Easy container is incredibly easy. However, there are some modifications that we’ll make.
1. After the container is started, access it by navigating to the IP address of your Unraid server and port 51821. Then, log in with the password you defined in the last step.
http://UNRAID_IP:51821
2. Select New Client to create a new client.
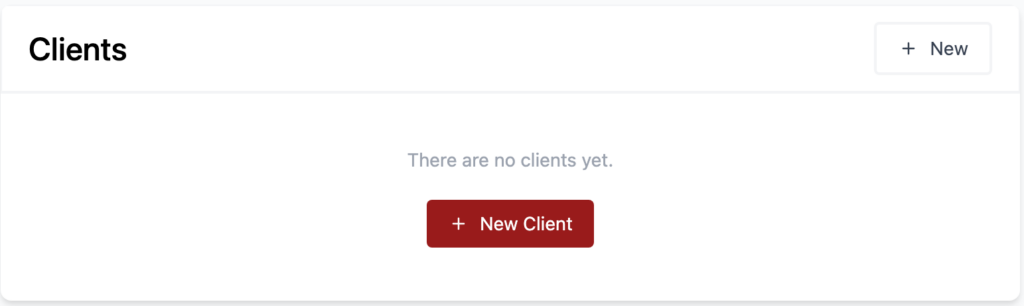
3. Enter a name for the client, then select create.
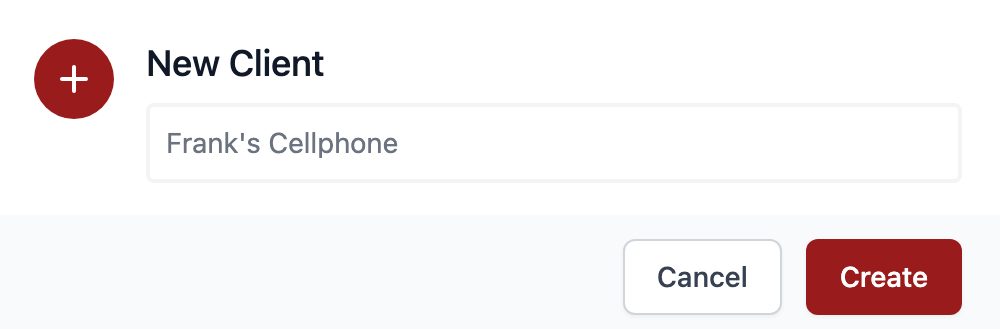
4. At this point, the client is technically created. However, we will make some modifications before attempting to connect. Depending on which device you’ll be connecting with, either download the configuration file or scan the QR code (generally done with the mobile app).
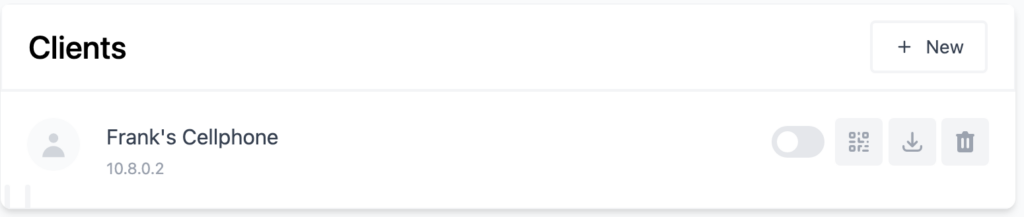
Configuration File Example
Scanned QR Code Example (Android WireGuard Application)
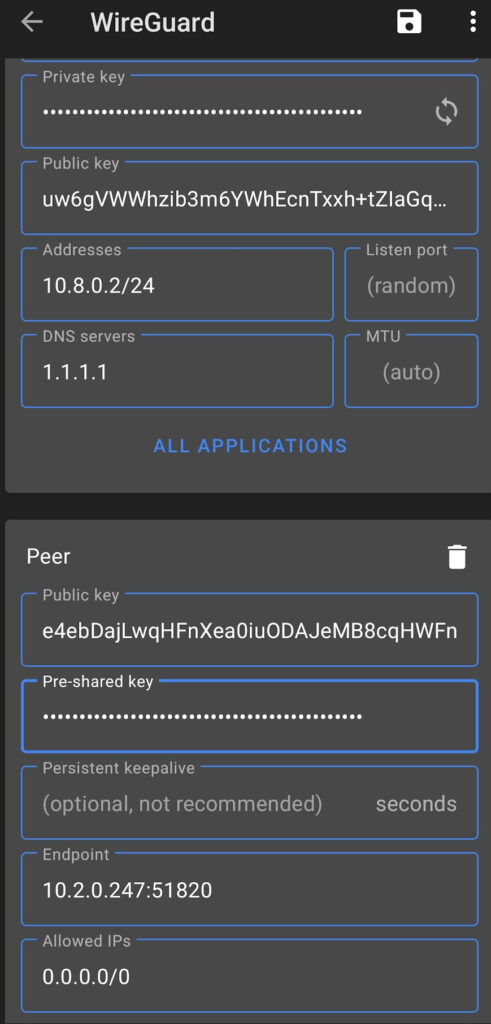
The first modification that must be made is to the Endpoint. If you have a static external IP address, you’ll have to change the Unraid servers IP address to your static external IP address.
STATIC_IP:51820
However, if you have a dynamic IP address (most people do), you’ll have to modify the endpoint to be your DDNS hostname and port 51820.
DDNS_HOSTNAME:51820
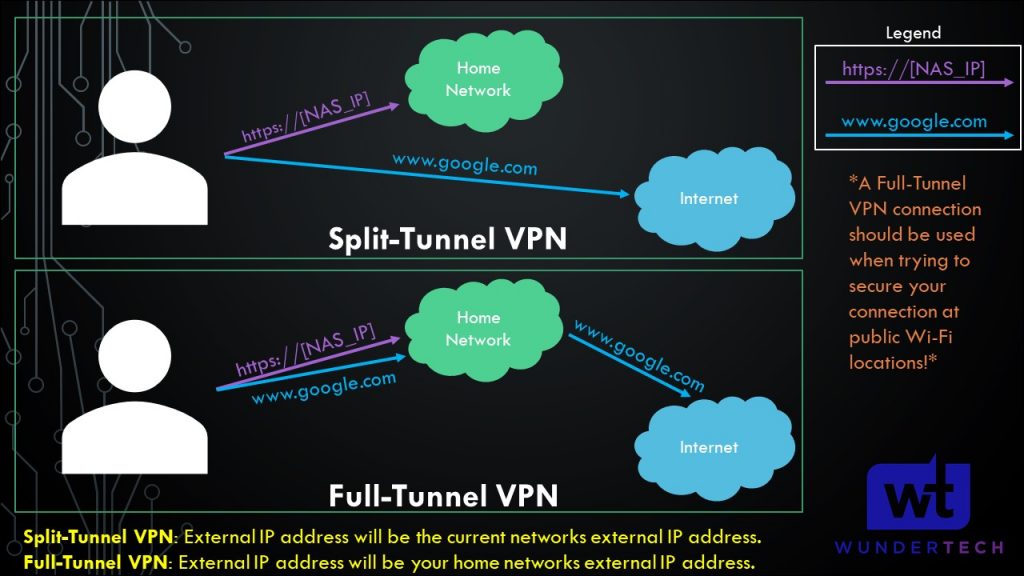
5. The next modification that must be made is to the AllowedIPs section. There are two types of VPNs that you can set up – split tunnel and full tunnel.
Split-Tunnel vs. Full-Tunnel for your WireGuard VPN
- Split-Tunnel VPN: Traffic is only sent through your network if it is attempting to access an internal resource. Your IP address when navigating to a site outside of your network will be the IP address of the network that you are currently on.
- Full-Tunnel VPN: All traffic is sent through your VPN tunnel. Your IP address for internal and external requests will be the network that WireGuard is set up on. I created a very basic image below that explains this.
It’s important to understand that both VPN types will allow you to access your local network. This only shows how traffic is routed differently to external networks.
NOTE: This is not the exact network flow. I am simplifying the process as much as I can.
Depending on which type of VPN you’d like to use (you can technically create one for both), modify the AllowedIPs parameter to reflect that.
- For a full tunnel VPN, set the AllowedIPs as 0.0.0.0/0.
- For a split tunnel VPN, set the AllowedIPs to be your local subnet or any subnets that you’d like this VPN tunnel to be able to access.
- For the example I am using above, I’d set the AllowedIPs as 10.2.0.0/24 so that the VPN can access everything on that subnet.
6. You should now be able to connect if you are on an external network! Depending on the type of VPN you set up, you’ll either have all traffic routing through the VPN (full tunnel) or only the local subnets you defined (split tunnel).
Conclusion & Final Thoughts on Unraid and WireGuard
This tutorial looked at how to set up WireGuard on Unraid. It’s very easy to get WireGuard working on Unraid. It’s also great to manage peers using the web client as it simplifies the process and only forces you to do the necessary steps. WireGuard is my favorite VPN protocol and is gaining tons of popularity as the years go on. If you’d rather run WireGuard on another device, please check out some of our other WireGuard tutorials.
Thanks for checking out the tutorial on how to set up WireGuard on Unraid. If you have any questions on how to set up WireGuard on Unraid, please leave them in the comments!




