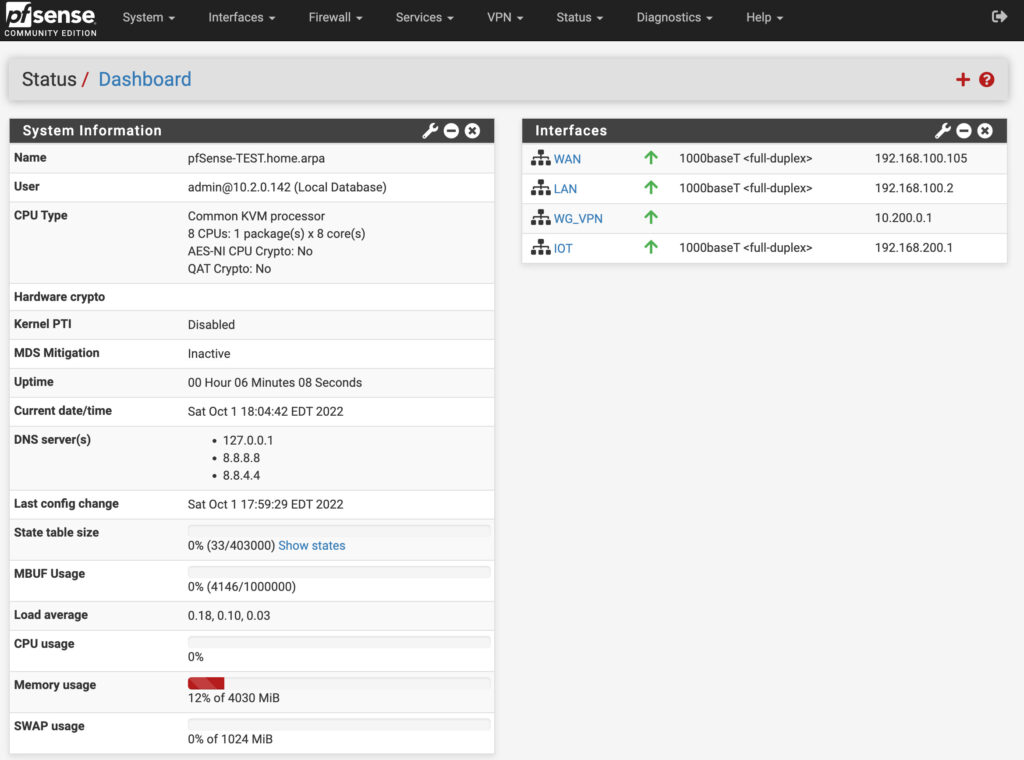
A question that comes up from time to time (and one that I spent a long time thinking about for a while) is if you should virtualize a firewall. I’m not talking about doing it for testing purposes – I am talking about running a firewall operating system like pfSense or OPNsense virtually and if it makes any sense whatsoever.
Should You Virtualize a Firewall?
As time has gone on, I’ve realized that there isn’t a single answer to this, and “it depends” seems to be the general response, but I want to try and break down why I once thought virtualizing a firewall was a great idea and why I am less inclined to recommend it these days. The answer comes from one word and one word only: updates.
If you’re using a firewall like pfSense or OPNsense, you’ll fall into their natural update schedule. That means that periodically, you’ll be updating the system based on the update schedule adhered to by the dev team.
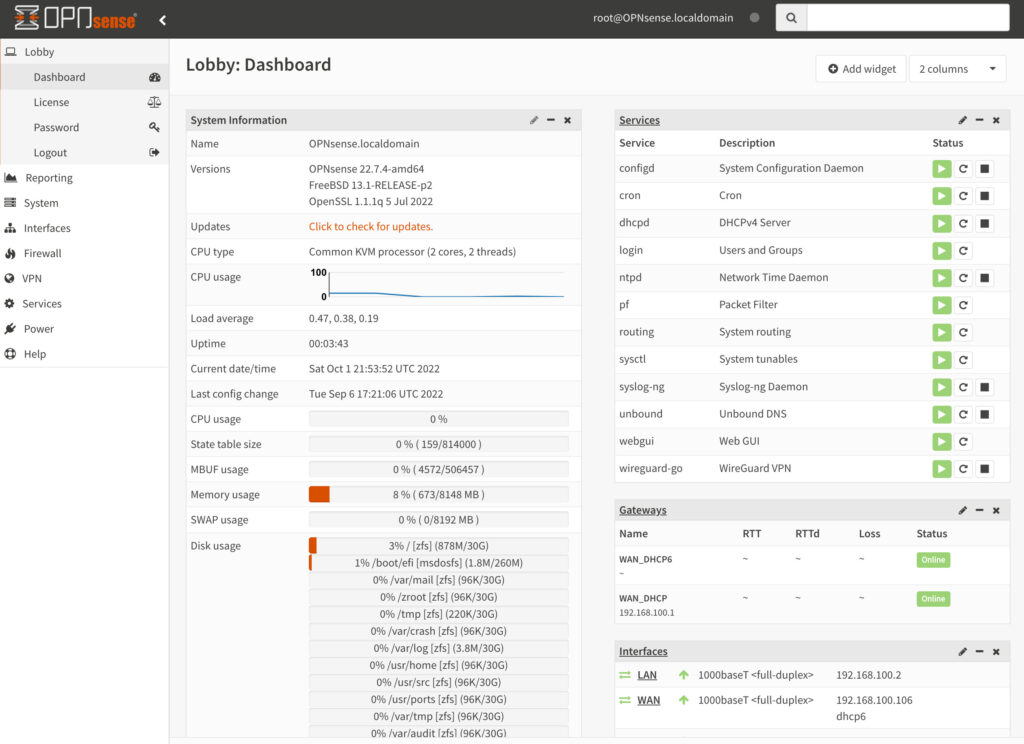
With dedicated hardware, the updates can be stressful because you’re using an appliance where problems may occur from the update, and if they do, you’ll generally be stuck troubleshooting that appliance to try and get it up and running ASAP.
With a virtualized instance of your firewall, you can wipe those concerns away as you’ll generally take a snapshot/backup right before installing the update and if there’s a problem, you’ll have an instant rollback plan. This will put you right back to where you were before the update was applied. This is incredible, but there are a few massive problems that must be considered with virtualized firewalls:
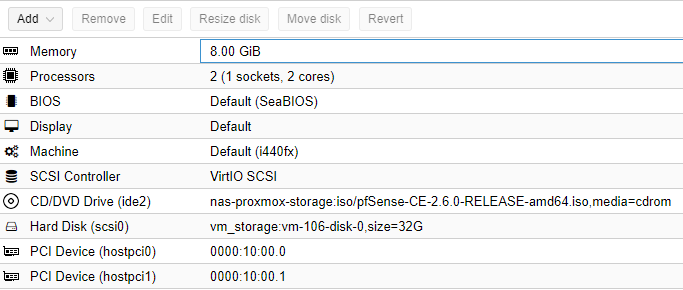
- The virtualized firewall is generally running alongside a set of other VMs/containers.
- The virtualized firewall is running on a hypervisor that requires updates as well.
- The virtualized firewall will generally have hardware passed through from the host to the guest.
These three points end up being a tremendous hurdle in a lot of cases, as hypervisor updates can require more frequent reboots than you’d like for a traditional firewall appliance to have, as well as potentially causing issues in the guest VM. They also add in unnecessary complexities, where hardware is passed through to the guest, and depending on how it’s done, can lead to PCIe passthrough issues.
Stick with a Dedicated Firewall Appliance
I played this game, and have a few different firewalls virtualized as test environments where they run great, but the firewall you use should be the most rock-solid device you own, and adding in the complexities of a hypervisor will only detract from that. While it’ll help with updates and rollback plans from those updates, the day-to-day issues that may arise can drastically impact that, so in my mind, stick with a dedicated firewall appliance.
