One of the most common questions I receive is how to access a Synology NAS remotely. One of the most natural follow-up questions after responding “the best way for most is to use a VPN”, is about which type of VPN they should use. Generally, there are self-hosted options and third-party options and they each have their own benefits which we’ll break down below
Do you have a Carrier-Grade NAT (CG-NAT)?
First and foremost, if you’re using a CG-NAT, it basically means that your ISP ran out of external IPv4 addresses to give to its users, and instead, gave them a private IP address. This means you can’t do any forwarding and a self-hosted VPN isn’t something that can easily be configured. In that case, using a tool like Tailscale will most likely be your best option as Tailscale doesn’t require port forwarding and a self-hosted VPN does.
Self-Hosted VPNs
There are two self-hosted VPNs that almost everyone out there uses – WireGuard and OpenVPN. Generally, you’ll configure these on your firewall or a device on your internal network, but you can run OpenVPN on a Synology NAS as well.
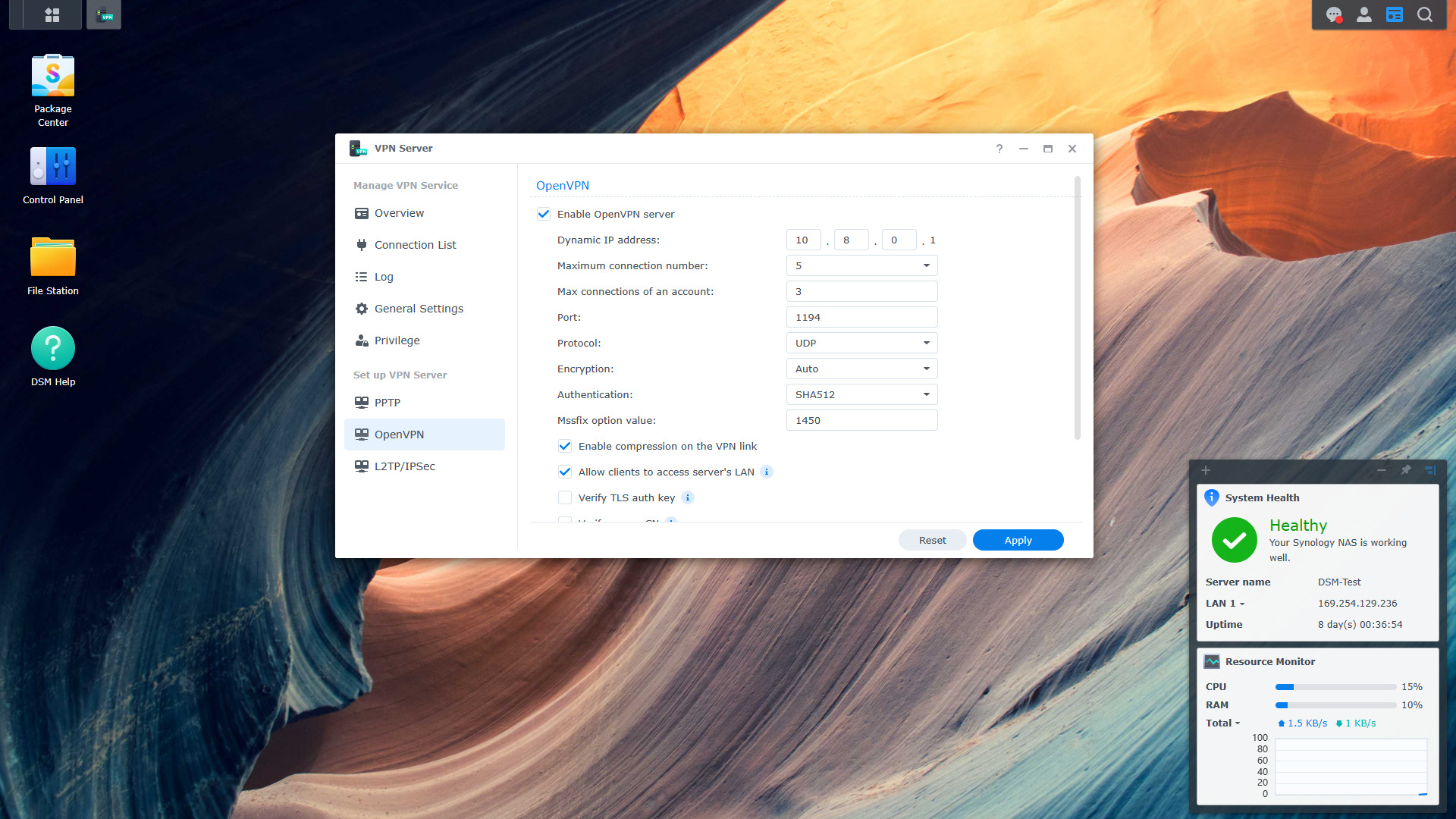
There are a few downsides to self-hosted VPNs:
- You’re responsible for everything (setup, config, updates, security, maintenance)
- The setup process is fairly involved for a beginner.
- You must be able to port forward (and understand what you’re doing)
However, there are a ton of great benefits as well:
- You manage everything and know exactly what is/isn’t connecting to your network.
- There are no third parties to worry about in terms of privacy and security.
- No fees whatsoever.
For this reason, most people prefer using a self-hosted VPN if they’re technically capable, can port forward, and plan on maintaining it. However, there are people who want a simple setup and that’s where a VPN like Tailscale comes in.
Tailscale
I say this every time I talk about Tailscale, but it’s the easiest VPN I’ve ever set up and you can configure it directly on your Synology NAS. If you put a timer on right now, I could have a fully functional Tailscale VPN running in less than 2-3 minutes.
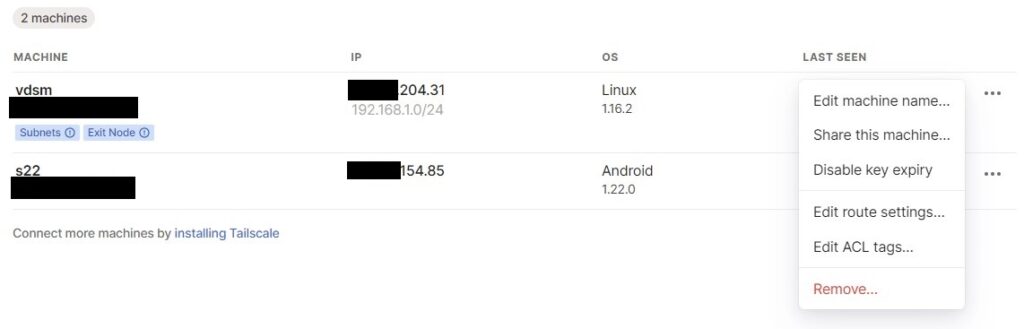
There are a few downsides, however, to running Tailscale:
- Everything is maintained on the Tailscale side, which means you’re working with a third party.
- If for some reason, the Tailscale console (which is hosted in the cloud) goes down, you will not be able to use your VPN.
- There may be fees depending on how many users/devices want to connect.
With that said, the benefits are strong as well:
- Extremely easy to set up on various devices.
- No port forwarding is required.
- Connecting multiple sites is extremely straightforward.
- Choose what does/doesn’t get exposed through Tailscale.
Final Thoughts: Self-hosted VPN or Tailscale?
I’m going to break this down as easily as I can. If you have a CG-NAT or don’t want to tinker, I’d suggest Tailscale. If you don’t and feel comfortable tinkering with a self-hosted VPN, I’d try either WireGuard or OpenVPN, depending on the system(s) you have available. Both are great options and while I prefer WireGuard (I run it on pfSense), I have used (and still have configured) OpenVPN for years. They’re both great options and you really can’t go wrong with either.